In an era of increasing digital threats and regulatory scrutiny, banks face mounting pressure to demonstrate robust cyber resilience. Regulations like the EU's Digital Operational Resilience Act (DORA) are raising the bar for how financial institutions manage information and communication technology (ICT) risks.
To meet these challenges, banks must adopt a structured approach to mapping critical business capabilities to the supporting IT resources. A credible framework must manage a traceable linkage across risk scenarios, business services, business capabilities, business processes, data, and underlying technologies, integrations and suppliers.
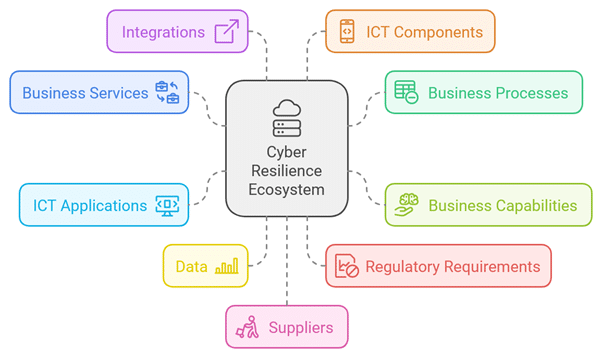
Some questions in this context include:
- which business services are in play for a specific business service?
- which business processes underlie each business service?
- which business capabilities are enabled by each business process?
- which ICT applications support these business process?
- which data can be manipulated by those applications?
- which specific data is subject to specific regulatory requirements?
- which integrations and network connections expose those applications to external actors?
- which underlying ICT components support those applications?
- which suppliers provide ICT components and services support those applications?
This article explores the importance of using standard reference models in this process and outlines a value stream for creating a compliant cyber resilience framework.
The Regulatory Landscape
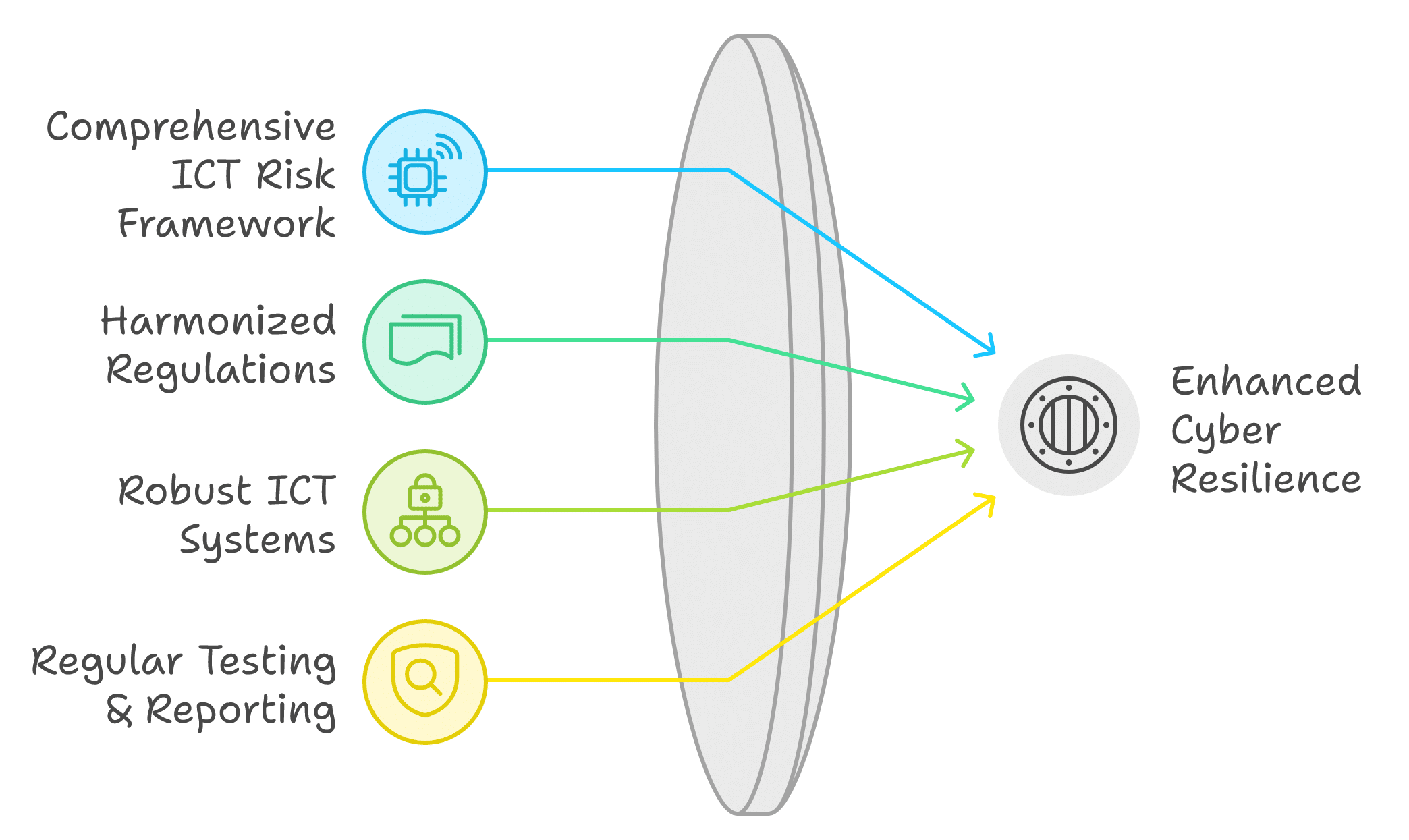
Before delving into the specifics of how banks can enhance their cyber resilience, it's important to understand the regulatory context. DORA, set to be enforced from January 17, 2025, exemplifies the trend towards more comprehensive and stringent ICT risk management requirements in the financial sector. While DORA is specific to the EU, similar regulations are being adopted or strengthened in other jurisdictions.
DORA and similar regulations aim to:
1. Establish a comprehensive framework for managing ICT risks in financial services
2. Harmonize existing regulations across different regions
3. Ensure that financial entities and their critical third-party providers maintain robust ICT systems
4. Mandate regular testing and reporting of cyber resilience measures
To comply with these regulations, banks must demonstrate that they have:
1. Identified their critical business services and the ICT systems supporting them
2. Implemented a comprehensive ICT risk management framework
3. Established processes for continuous monitoring, testing, and improvement of controls
4. Created robust incident response and reporting mechanisms
While these requirements may seem daunting, adopting a structured approach using standard reference models can significantly streamline the compliance process and enhance overall cyber resilience.
A Value Stream Approach to Cyber Resilience
To create a compliant framework for cyber resilience, banks can follow a value stream approach consisting of three main stages:
1. Identify enablers for critical business services
2. Establish or improve relevant risk management frameworks
3. Uplift the technology landscape and apply the control framework
Let's explore each of these stages in detail, highlighting the role that standard reference models, particularly the Banking Industry Architecture Network (BIAN) model, can play in simplifying and standardizing the process.
Stage 1: Identify Enablers for Critical Business Services
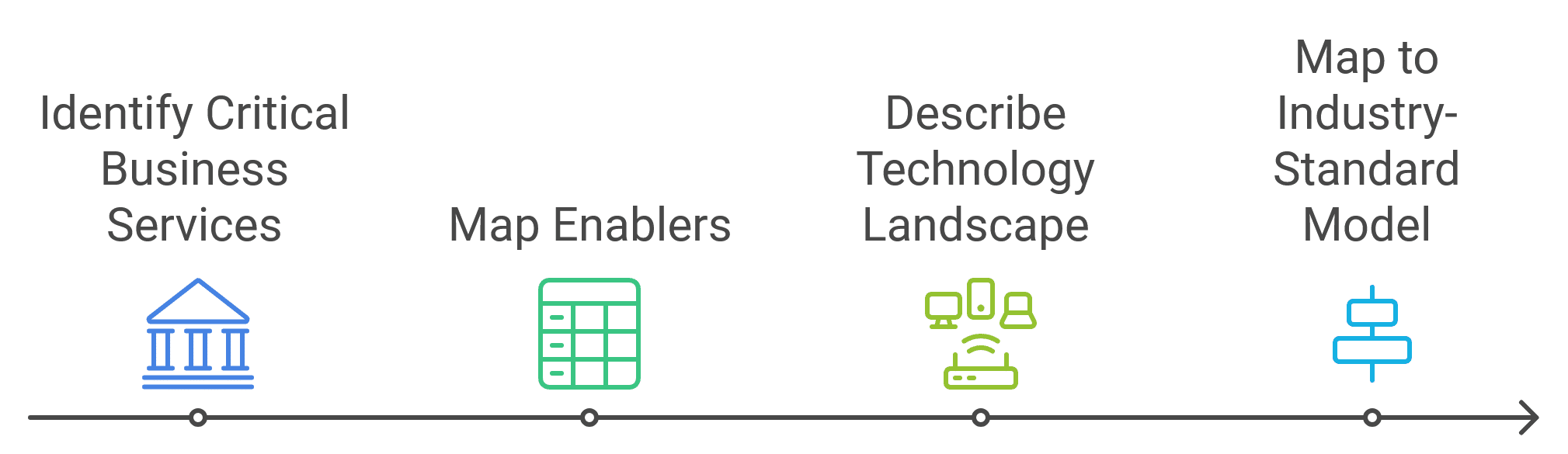
The first and perhaps most crucial step is identifying which critical business services fall within the scope of compliance requirements. This involves:
a) Identifying critical business services: Banks must determine which of their services are essential to their operations and to the broader financial system. Among the most obvious candidates are payment processing, lending, or trading services.
b) Mapping enablers: Once critical services are identified, banks must map out the business processes, data, and applications that support these services. This often proves challenging due to the complex, interconnected nature of banking systems.
c) Describing the technology landscape in terms of business functions and capabilities: The semantic integrity of the mapping requires that identified enablers must be described in a standardized way, focusing on the business functions they support and the capabilities they provide.
d) Mapping to an industry-standard capability model: This is where a standard reference model becomes invaluable. By mapping their specific and consistently defined processes, data, and applications to an industry-standard model like BIAN, banks can ensure consistency and completeness in their assessment.
The BIAN Service Landscape as a Standard Reference
The BIAN (Banking Industry Architecture Network) service landscape offers a comprehensive, industry-standard capability model that can serve as an excellent reference for this mapping process. Using BIAN as a proxy for an industry-standard capability map provides several advantages:
1. Common language: BIAN provides a standardized vocabulary for describing banking functions and capabilities, reducing misunderstandings and improving communication both internally and with regulators.
2. Completeness: The BIAN model covers the full spectrum of banking operations in most jurisdictions (with the notable exception for now of Islamic banking), helping ensure that no critical areas are overlooked in the mapping process.
3. Industry alignment: As an industry-standard model supported by top-tier global institutions, BIAN reflects best practices and common structures in banking, making it easier to benchmark and compare with peers.
4. Flexibility: While comprehensive, the BIAN model is also flexible enough to accommodate bank-specific nuances and innovative services. The architecture is designed to be extensible into non-banking business areas such as insurance, and into technology areas such as the IT4IT and ITOM spaces.
By leveraging the BIAN service landscape, banks can more easily identify gaps in their current capability mapping and ensure a thorough assessment of their critical business services and supporting IT resources.
Stage 2: Establish or improve relevant risk management frameworks
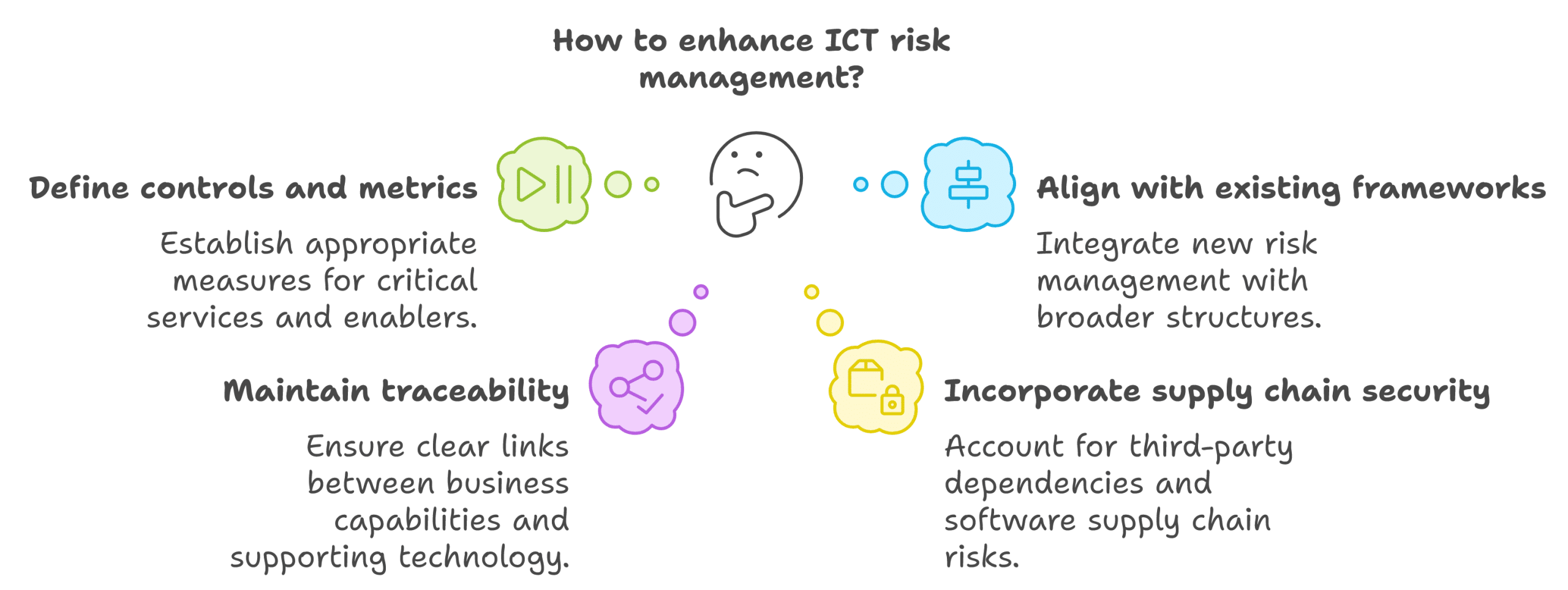
Once the critical business services and their enablers have been identified and mapped, the next stage is to establish a robust risk management framework as part of the larger corporate risk management approach. This involves:
a) Defining controls and metrics: Based on the identified critical services and their enablers, banks should define appropriate controls and metrics to manage and measure ICT risks.
b) Aligning with existing frameworks: The new risk management framework should not exist in isolation but should be integrated with the bank's broader risk management structures.
c) Maintaining traceability: It's crucial to maintain clear links between business capabilities and the technology that supports them. This is essential for effective risk management and for demonstrating compliance to regulators.
d) Incorporating supply chain security: Modern banking relies heavily on third-party providers. The risk management framework must account for these dependencies, including considerations like Software Bill of Materials (SBOM) for understanding and managing risks in the software supply chain.
The Role of Standard Models in Risk Management
Here again, standard reference models like BIAN can play a crucial role:
1. Standardized risk categorization: BIAN's service domains can serve as a basis for categorizing and assessing risks consistently across different areas of the bank.
2. Control mapping: The BIAN model can help in mapping controls to specific service domains and business objects, ensuring comprehensive coverage.
3. Metric alignment: By aligning risk metrics with BIAN's standardized service centers, banks can ensure they are measuring the right things in the right places.
4. Supply chain visibility: The BIAN model's comprehensive view of banking operations can help in identifying and managing third-party dependencies more effectively.
Stage 3: Uplift the technology landscape and apply the control framework
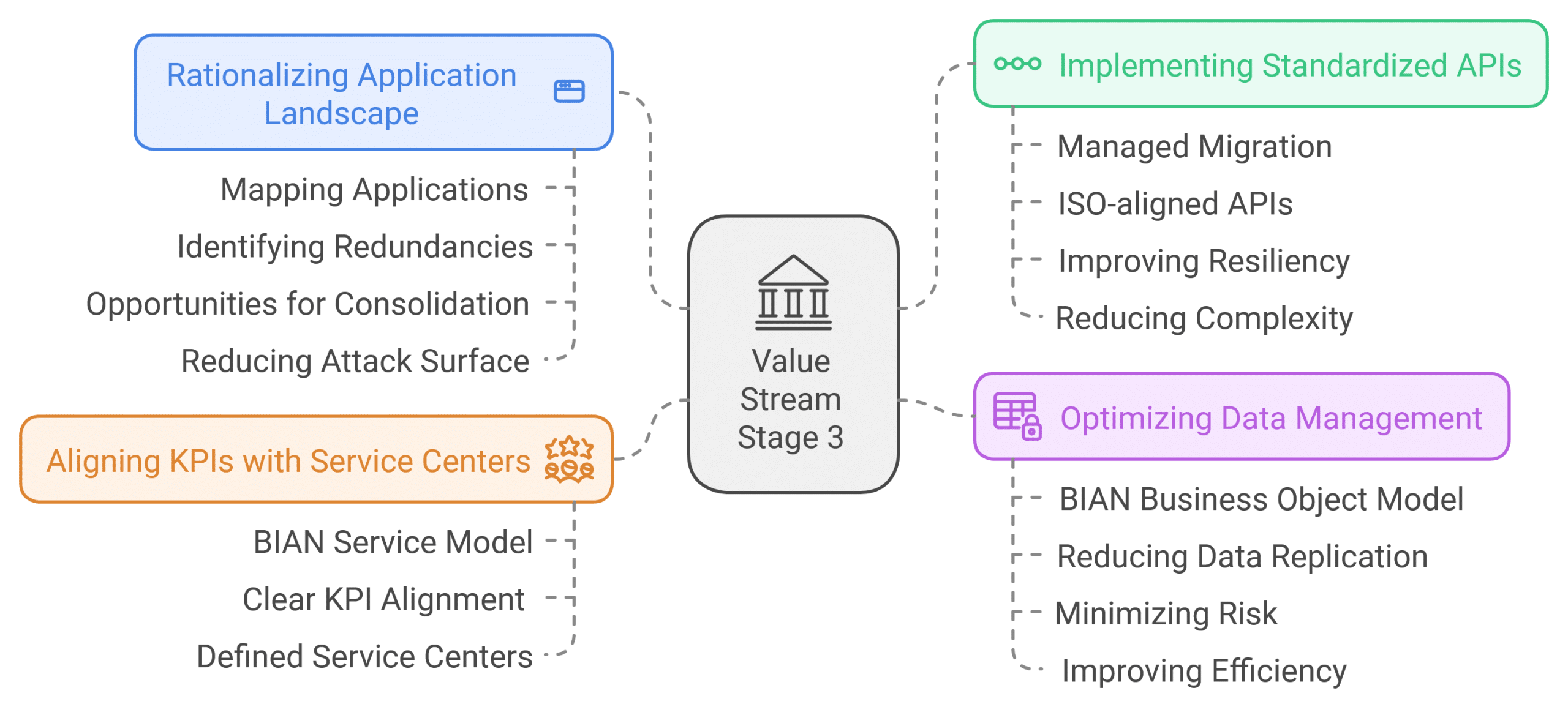
The final stage involves using the insights gained from the previous steps to enhance the bank's technology landscape and control framework. Key activities include:
a) Rationalizing the application landscape: By mapping applications to standardized capabilities, banks can identify redundancies and opportunities for consolidation, thereby reducing their attack surface.
b) Implementing standardized APIs: A managed migration to ISO-aligned, standardized APIs can improve resiliency and reduce complexity in the system landscape.
c) Aligning KPIs with service centers: Using the BIAN Service Model architecture can help to ensure that key performance indicators (KPIs) are clearly aligned with defined service centers.
d) Optimizing data management: The BIAN business object model can guide efforts to reduce unnecessary data replication, minimizing risk and improving efficiency.
Leveraging BIAN for Technology Uplift
The BIAN model provides several advantages in this stage:
1. Application rationalization: By mapping applications to BIAN service domains, banks can more easily identify functional overlaps and opportunities for consolidation.
2. API standardization: BIAN's work on API standards aligns well with efforts to implement standardized, resilient interfaces between systems, including Open Banking and other regulatory and ISO standards for banking APIs.
3. KPI alignment: The clear definition of service centers in the BIAN model facilitates the alignment of performance indicators with specific business capabilities.
4. Data optimization: BIAN's business object model provides a reference for optimizing data structures and reducing redundancy across systems.
Ongoing Monitoring and Incident Management
The work done in these three stages enables more effective ongoing monitoring, incident management, and reporting. By having a clear, standardized map of critical business services, their supporting IT resources, and associated risks and controls, banks can:
1. More quickly identify the business and security impact of IT-related incidents
2. More effectively prioritize incident response efforts
3. Provide more meaningful reports to management and regulators
4. Continuously improve the bank’s cyber resilience posture
The Value Stream in Action
Running the value stream is not a one-time effort.
It can be triggered by large-scale requirements for improving the risk framework, such as new regulatory requirements like DORA or significant changes to existing requirements that may be mandated by the regulators or inferred from regulatory or judicial activities.
The value stream should also be more routinely applied on a smaller scale in response to changes in the bank’s process and application landscape, such as the introduction of new applications or business processes, retirement of old systems, or significant updates to existing integrations and information flows.
By using a standard reference model like BIAN consistently across these activities, banks can ensure that cyber resilience efforts remain aligned and effective over time, even as their technology landscape evolves.
Conclusion: The Power of Standardization in Cyber Resilience
As regulatory requirements for cyber resilience in banking continue to evolve and become more stringent, the importance of a structured, standardized approach to managing ICT risks cannot be overstated.
By adopting a value stream approach underpinned by industry-standard reference models like BIAN, banks can:
1. More easily identify and map their critical business services and supporting IT resources
2. Establish more comprehensive and consistent risk management frameworks
3. Optimize their technology landscapes to enhance resilience and reduce complexity
4. Enable more effective ongoing monitoring and incident management
5. Demonstrate compliance more convincingly to regulators
While the task of enhancing cyber resilience may seem daunting, especially in the face of regulations like DORA, the use of standard reference models provides a clear path forward. By leveraging industry-standard frameworks, banks can not only meet regulatory requirements more efficiently but also build a stronger, more resilient foundation for their digital future.
As the financial sector continues to evolve and face new challenges, those institutions that embrace standardization in their approach to cyber resilience will be best positioned to thrive in an increasingly digital and interconnected world.